In my previous post on Vault, I showed how Hashicorp’s Vault can be used to protect important passwords, static passwords that don’t change frequently. Vault can do much more than this and can even automatically create temporary accounts and rotate passwords for database users.
Today, I’m using long-lived passwords that I generate once when I add a new service, I, along with most people, just insert those passwords into the environment like this:
| |
That’s not secure at all. While you can store them in Kubernetes Secrets, they’re not encrypted by default. Kubernetes can encrypt secrets, but they’re open to anybody with access to the cluster. The passwords are easily accessible to anybody with access to Kubernetes and are never rotated. This simply won’t do. In this post, I’m going to walk through how I switch to Vault for
Postgres
Vault natively supports Postgres and can either maintain the password for a single Postgres role and rotate the password periodically (called static), or generate a new role for every single Pod that runs (dynamic.) With static, I have to go into DataGrip and create a role and setup the permissions manually, but dynamically should be able to create it all for me.
If you haven’t already created a Database backend, create one (Vault docs) using the UI or the API. Add a connection to your database. Make sure to use a privileged user with the ability to create users. I just use the postgres super user account.
I can’t figure out dynamic roles
Dynamic roles in postgres were confusing. I couldn’t figure out how to grant privileges in a given database. I was able to create my user with the following creation statements, but no matter what I tried it
| |
It would grant CONNECT to the db:
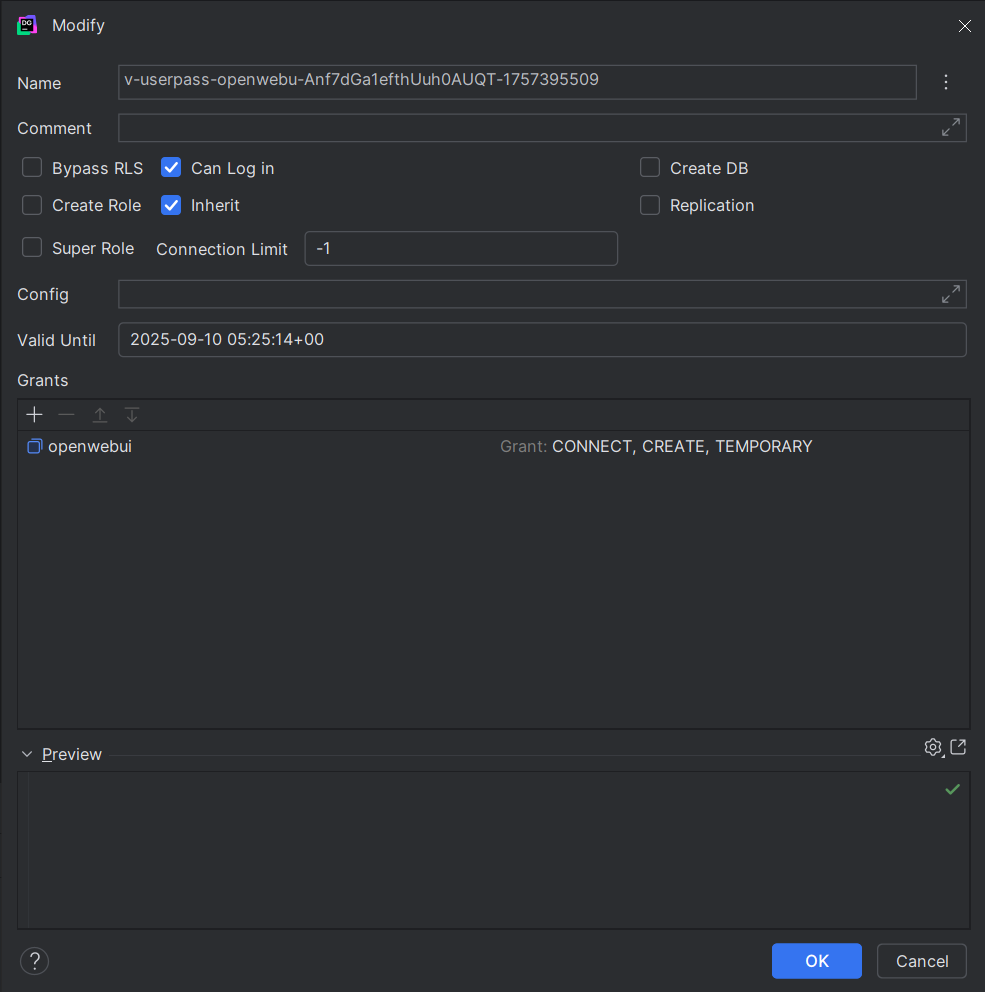
But this was insufficient to actually connect to the database and create/edit tables. Apparently Postgres configures the database at the connection level and does not allow me to grant this.
| |
Use a role
Looks like I can’t avoid pre-configuring the roles with Postgres. First, create a new role and grant it all appropriate privileges on the database:
| |
Bring it all together
Then create a Vault dynamic user like so:
- Role Name: Whatever you want or namespace/serviceaccount. This naming convention will be important if you’re following my guide
- Connection Name: Your PGSQL connection
- Type of Role: dynamic
- Creation Statements
| |
Now, if I click “Generate credentials” in Vault, I should get credentials that I login using DataGroup and view/edit table table.
Vault
Create the Vault role
So far, we’ve just created a secret that Vault can return, but our Kubernetes services can’t access these credentials, so we need to create a policy that allows a Vault user to access this Vault secret.
My previous approach of creating a new Kubernetes role and custom policy for every single Kubernetes service was become onerous. I want the ability to be able to add a new service to Vault without having to go through this work. If only services could automatically get access to their own secrets without being able to see other secrets. It’s possible with templated policies.
First, let’s create a common role in the Kubernetes authentication method that every pod can assume.
- Authentication Method: Kubernetes
- Name: k8srole
- Alias name source: serviceaccount_name
- Bound service account names: *
- Bound service account namespaces: *
NOTE: Don’t assign any privileged policies because any service will be able to assume this role. If you want to be more careful, explicitly list the namespaces that run services that should have access in the role.
Create the Vault Policy
When I first started, I didn’t fully understand how templated policies in Vault worked. There were these parameters that I could use, like identity.entity.id, but it’s not clear how that looks in Kubernetes.
| |
To figure this out, I launched a pod with this Vault approle, and pulled the token out of /vault/secrets/token. Then used curl to call the API.
| |
That returned:
| |
Then I fetched more details using the data.entity_id parameter:
| |
| |
Say I want to limit my policy to be able to access secrets named {{namespace}}|{{service_account_name}}, I use these parameters:
{[namespace}}={{identity.entity.aliases.auth_kubernetes_398dc4e7.metadata.service_account_namespace}}. Theauth_kubernetes_398dc4e7is the name of the auth method specified inmount_accessor{{service_account_name={{identity.entity.aliases.auth_kubernetes_398dc4e7.metadata.service_account_name}}
Final Policy
Assuming I have a database storage end called database, I can grant access by creating a policy:
| |
And if I want to grant read-only access to secrets under by-service/{{namespace}}/{{service_account}}/*
| |
NOTE: Your auth provider name will be different than auth_kubernetes_398dc4e7. Make sure you update it.
Create a policy with the above directives and name it something like k8s-default-policy. The go back to the Kubernetes role k8srole and add the policy under Generated Token’s Policies.
Using it in an app
How you get an app to use the Vault credentials will differ depending on the app itself.
Using environment variables
For applications that take the password using an environment variable and can’t use a file, I use Vault’s templating system to generate a file called /vault/secrets/env, then source it and invoke the process as normal.
For example, with OpenWebUI, I would do:
| |
This generates a file that looks like:
| |
Using files
Files are the easiest way. For example, Authelia can be configured using:
| |
Conclusion
Thus far, I’ve create a reusable Vault role and Vault policy that that any Kubernetes pod with a service account can assume and login to Vault. It will only have access to secrets that match it’s name. Now it’s easy to onboard new services and grant secure access.
